Contributor: Robin Wilton
The Internet is a critical, global resource that brings incredible benefits, provided it is both accessible and trustworthy. In 2020, the Internet Society identified five critical properties that ‘make the Internet the Internet’. They represent the foundation of the Internet, which we call the Internet Way of Networking (IWN). Without them, the Internet’s benefits of global innovation and opportunity are in jeopardy. The path from critical properties to global benefits involves risk, however, and encryption is a vital tool for protecting ourselves along the way.
Cryptographic technology, including encryption[1], protects the integrity and confidentiality of data; it underpins authentication protocols and digital certificates. It secures communication protocols and protects access to resources and data-at-rest.
Cryptographic tools are used throughout the Internet’s technical architecture, both to encrypt data and communications to provide confidentiality, and to verify the integrity of key parts of the Internet’s infrastructure, such as naming and addressing systems. Cryptographic tools enable basic functionality and make possible many of the capabilities that amplify the Internet’s greatest benefits. Individuals, families, businesses and countries worldwide rely on confidential communication, secure transactions, and the safety of connected vehicles and devices. If encryption is unavailable or unreliable, Internet connectivity is hampered by added costs and burdens, and the ecosystem as a whole suffers from increased risk and reduced trust.
This analysis is intended to help policymakers worldwide understand how encryption operates throughout the Internet’s infrastructure, and not just in the applications so many of us use each day. It explores the positive and mutually reinforcing interaction of encryption with the Internet’s critical properties, and the way this amplifies the Internet’s benefits for all.
Encryption and IWN Critical Property 1: An Accessible Infrastructure with a Common Protocol
Graphic 1: “Critical Property 1 and its Benefits”
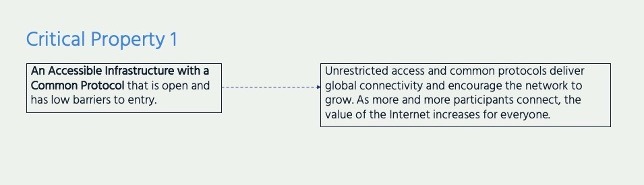
The Internet’s growth and global reach are made possible by an accessible infrastructure with a common protocol, the Internet Protocol (IP), which allows any device, network or server to connect to the Internet. While other physical connection types exist in the technical layer ‘beneath’ the IP layer, and a wealth of protocols has been built on top of it, the IP layer connects them all with an open standard that applies across the entire, global Internet.
However, greater openness can introduce higher risk. For example, the original HTTP (Hyper Text Transfer Protocol) enables access to interconnected data, but does not protect communications from eavesdropping, or from ‘machine-in-the-middle’ attacks where a third party impersonates the endpoints to intercept or alter communications. This vulnerability made financial transactions on the web risky, so the technical community developed HTTPS (Hypertext Transfer Protocol Secure), which uses session-level encryption to protect the confidentiality and integrity of communications and thus secure online commerce and other interactions.[2]
Being able to mitigate or reduce the security risks inherent in an accessible infrastructure means we can continue to innovate and enjoy an open, globally connected network whose value continues to increase with its size.
Encryption is a technological building block that fits in with the overall Internet architecture and can work to mitigate risks without compromising the openness of the Internet. If encryption was unavailable or unreliable, these mitigations would not be possible. We could not be sure that a website’s domain name is authentic. Online commerce simply would not work. We need strong, reliable encryption to support current and future innovation, so we can enjoy the benefits of an Internet whose value increases with its size and reach, and which now forms a critical part of national infrastructures and the global economy.
Encryption and Critical Property 2: Open Architecture of Interoperable and Reusable Building Blocks
Graphic 2: “Critical Property 2 and its Benefits”
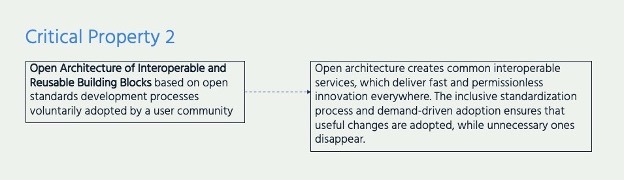
The relation of encryption to Critical Property 2 – an open architecture of interoperable and reusable building blocks – is the reverse. Instead of encryption directly enabling the Internet’s open and modular architecture, the permissionless and responsive innovation the Internet allows means encryption can be applied wherever it is needed. Each existing ‘building block’ delivers a specific function, such as supporting different network types, ensuring reliable transport or providing name resolution.[3] The open architecture itself is an enabler of multiple, responsive applications of encryption, and the open standards development process drives a constant evolution of useful services.
For example, a manufacturer of connected home sensor systems does not need to re-invent, from scratch, secure authentication protocols for its remote devices. Instead, the manufacturer can rely on open specifications developed and scrutinized by an expert and global technical community over many years.[4] Each innovator who needs to use a cryptographic method like hashing or digital signing can access existing and publicly available work; a crucial enabler given the complexity of encryption and the potentially severe implications of getting it wrong.
The Internet’s architecture of interoperable and reusable building blocks also makes the resulting systems more agile and responsive to emerging security requirements than a closed or monolithic system might. For example, if an encryption algorithm is broken, the application or functionality that depends on it will likely be quicker and easier to secure if just the encryption component needs to be replaced, and not the entire application or communication protocol. In deployments of cryptographic technology, “algorithmic agility”, or the ability to replace a compromised technology with a safe alternative, is not just good practice, it is a critical enabler of security and therefore trust.
Sometimes, however, the Internet’s architecture of reusable building blocks is “necessary but insufficient”, especially when user convenience or different business models are the overriding factor. Email provides an example of how users’ desire for convenience can override their wish for security. Email was originally developed simply to send communications across the Internet – unencrypted. It is not an inherently secure way to send messages, and it is still also relatively easy to ‘spoof’ the sender’s address. While many encryption-based innovations respond to these issues, the barriers to adoption are usability, not security. Encryption makes it possible to send and receive email securely to and from anywhere in the world – and with assurance about the sending address and the integrity of the email itself. But the inconvenience and difficulty of public key infrastructures, for example, are off-putting to most average users.
Overall, though, encryption and the Internet’s open architecture and reusable building blocks are mutually reinforcing, in ways that multiply the Internet’s benefits for everyone.
Encryption can be added onto or completely integral to a building block, in ways that extend the trustworthiness and functionality of an ever-increasing array of services. The Internet’s ‘value-added’ services are secured and enabled by encryption, and the continued evolution of both the infrastructure and all the innovation it supports can be assured.
Encryption and Critical Property 3: Decentralized Management and a Single Distributed Routing system
Graphic 3: “Critical Property 3 and its Benefits”
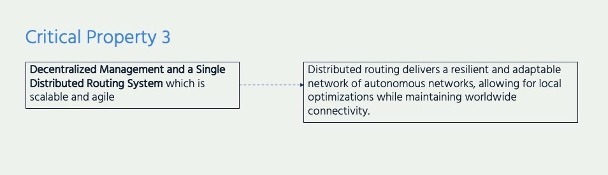
The Internet is a ‘network of networks’ made up of almost 70,000 autonomous systems that individually decide how to route their own data and connect with each other. No central authority determines which routes data should take between the thousands of networks that comprise the global Internet. Each network optimizes decisions on how to route traffic to suit its own local needs and conditions. This decentralized system maximizes autonomy and agility, supporting a globally connected Internet adapted to many different settings.
Cryptographic tools directly support this critical property by providing networks with a trusted way to talk to each other. Each network needs to be able to check that routing announcements – the instructions a network issues to say it is authorized by the owners of other networks to route traffic to them – are legitimate. One solution is to set up a Resource Public Key Infrastructure (RPKI), so that a network can publicly ‘sign’ the routing announcements it makes, and other networks can verify their authenticity and ensure their content has not been interfered with.
RPKI uses cryptographically signed certificates to:
- Bind a resource (a block of the IP address space) to the autonomous system authorised to announce it; and
- Protect the integrity of routing announcements as they are exchanged between autonomous systems or networks.
Without RPKI or a functional equivalent, there is no secure way for networks to validate that other networks they exchange traffic with are authorized (by the holders of the destination addresses) to forward traffic to these destinations. Nor is it possible to ensure that routing instructions have not been interfered with. There is a higher risk that traffic would not reach the correct destination, either through error or because of an attack based on the impersonation of the recipient.
Without the cryptographic tools that strengthen its trustworthiness, the benefits that the distributed routing system delivers – global reach, resilience, and optimized connectivity – are at risk.
The decentralized management of the networks could be undermined, as the decision the networks take about how to interconnect and where to forward traffic could be based on incorrect or falsified information.
Cryptographic tools support connectivity between autonomous systems by increasing the trustworthiness of their interactions. RPKI is just one example of cryptographic mechanisms being used to underpin Critical Property 3. Another example is the use of cryptographic mechanisms for authentication and integrity protection of routing information among neighbouring networks[5]. If these and similar mechanisms are absent or unreliable, the pathway to the Internet’s benefits is broken, as connectivity between networks suffers. The benefits that Critical Property 3 unlocks – the agility and reach that local network decision-making on routing brings – would recede, leaving us with a less trustworthy, reliable and scalable ‘network of networks’.
Encryption and Critical Property 4: Common Global Identifiers
Graphic 4: “Critical Property 4 and its Benefits”
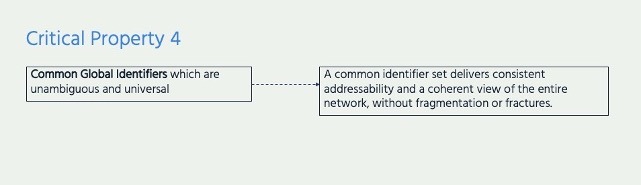
IP addresses and the domain names are the ‘glue’ that hold the Internet together, ensuring every data packet gets to where it is meant to go, anywhere in the world. The domain name system (DNS) translates web addresses into IP addresses (each of which is a series of numbers), and the IP addresses are used to bring the Internet user to the right destination.
The critical property of common global identifiers delivers all the benefits that flow from a consistent, universal and reliable service to every Internet user. These global identifiers are also the piece of infrastructure that everyday Internet users recognise or interact with directly. If the Internet’s unique identifiers became inconsistent or ambiguous, communications would be misrouted or simply fail, and malicious entities could easily masquerade as other sites or senders.
The DNS is a distributed system; mapping domain names to IP numbers involves many different entities. These include:
Any of these entities can be compromised, with the result that DNS queries and responses can be intercepted and modified, misleading users and sending them to a malicious site and exposing them to other kinds of attack.
Similarly to Critical Property 1, the strength of an open and distributed system such as the DNS is its scale, but its weakness can be the vulnerabilities that openness creates. Cryptographic tools are used to secure and validate the integrity of the DNS, which helps mitigate these risks by securing the integrity of the distributed addressing system.
DNSSEC is a suite of security extensions to ensure the integrity of data from the DNS registry, through the chain of authoritative servers to the recursive resolver and ultimately the Internet user. At its simplest, DNSSEC allows the registry for each Top Level Domain (for example, .COM or .ORG) to cryptographically ‘sign’ its results, certifying their integrity. DNSSEC is an example of how Critical Property 2 enables the use of different building blocks throughout a distributed and interoperable system.
Although DNSSEC deployment can be challenging, its widespread and growing use supports the global reliability of domain names and increases the trustworthiness of a key part of the Internet’s fundamental architecture.
Encryption protects the path to future benefits of the Internet.
With cryptographic technology, we can secure communications, data, and access to resources. We can check the identity of the people and services we are connecting to, and we can entrust data to third parties knowing that it is safe from snooping and tampering. Without it, existing services become unsafe, and future innovation is constrained.
These principles apply to the Internet infrastructure as much as they apply to our everyday use of it, and they are intimately related to the Internet’s Critical Properties. For instance, encryption forms a ‘virtuous circle’ with Critical Property 2, because the Internet’s distributed and interoperable architecture makes it possible to adapt and complement reusable building blocks with cryptographic tools, and so to respond innovatively to challenges and opportunities.
Endnotes
[1] In this document, we use “encryption” as shorthand for the set of related data security tools providing confidentiality, integrity and digital signatures, unless specified otherwise.
[2] Retail e-commerce alone accounted for almost $3 trillion in 2018: https://99firms.com/blog/ecommerce-statistics/
[3] Examples of the building blocks include protocols for wireless networks such as IEEE802.22, or TCP (Transport Control Protocol) which ensures reliable data transport between systems.
[4] https://datatracker.ietf.org/wg/ace/about/
[5] For instance, work to add authentication and integrity checks to TCP is described in RFC5925: https://tools.ietf.org/html/rfc5925